In terms of cybersecurity, the impact of the COVID-19 crisis has been harsh and felt by all organisations, whatever their size. Even if parameters such as the degree of use of the Cloud or the habit of teleworking enabled some organisations to better manage the current crisis, they had to take immediate action to maintain a minimum level of security.
As the horizon is becoming clearer, they must focus their efforts on regaining control over their security and launching priority projects to meet the challenges of the coming months.
An increased cyber risk during lockdown
Faced with an increased and constantly evolving threat, the cybersecurity workforce is under great strain. They have had to cope with the necessary reduction in security to facilitate new uses and actions made more complex by the context in which their organisation operates (absence of teams and service providers, difficulties in working remotely, etc.).
In an initial, very short preparation phase before the government measures were triggered, the cybersecurity teams worked on immediate measures to ensure their activities, while adapting to the circumstances and sometimes reducing the level of security.
- Raise employee cybersecurity awareness (phishing, CEO fraud, strength of passwords, data leakage, etc.) and keep them informed of any changes during the crisis
- Track security derogations, assess the impact and explain the residual risk to the business (administration rights on workstations, use of tools or USBs, reduction of authentication requirements, postponed installation of patches, authorization of split tunneling, etc.)
- Capitalize on feedback by connecting to its cyber ecosystem
- Detect and understand new uses (use of unmastered third party applications to ensure the offering of appropriate solutions now and in the future)
- Implement additional security solutions if necessary (strong authentication via mobile, securing RDP flows, password management solutions, secure messaging for VIPs, VDI farms for the use of BYOD equipment, etc.)
- Adapt monitoring capabilities to the situation (focus SOC efforts on critical applications, create specific detection scenarios for lockdown, continuously audit remote access systems, etc.)
- Urgently consider security continuity (crisis management whilst teleworking, separation of teams, tools, emergency instructions, information sharing, remote availability and access from third parties, remote evidence collection, etc.)
- Gather key information and decisions in order to give feedback on the crisis (access to knowledge, tools, management methods, impact of border closures, information sharing between geographical locations, etc.)
Now that this initial reaction phase has been completed, the cybersecurity teams must now focus their efforts on two upcoming challenges: regaining control and addressing the major challenges of the coming months.
Taking back control
Regaining control affects all areas of the information system:
Resecure Data
Identify and then save or erase the data disseminated on professional and/or personal workstations (or even health data collected on employees), providing clear instructions and tools to employees.
Reinforce systems and infrastructure security
Reducing machine administration rights, restoring disabled security mechanisms, security equipment filtering rules, anticipating the securing of potentially compromised machines upon their return, as well as the postponed application of server security patches, updating security policies to take into account new practices and risks.
Check the absence of intruders
Launch Threat Hunting operations to ensure that the old and new perimeters were not compromised during these moments of weakness.
In most cases, many derogations have been granted to allow remote working: access to applications with little security, deactivation of certain mechanisms such as strong authentication, administrative rights to use printers at home, use of uncertified tools (especially for videoconferencing) etc…
Organisations that have not maintained a list of these security derogations will first have to identify the derogations and then progressively correct them before the lifting of lockdown measures while allowing remote business continuity.
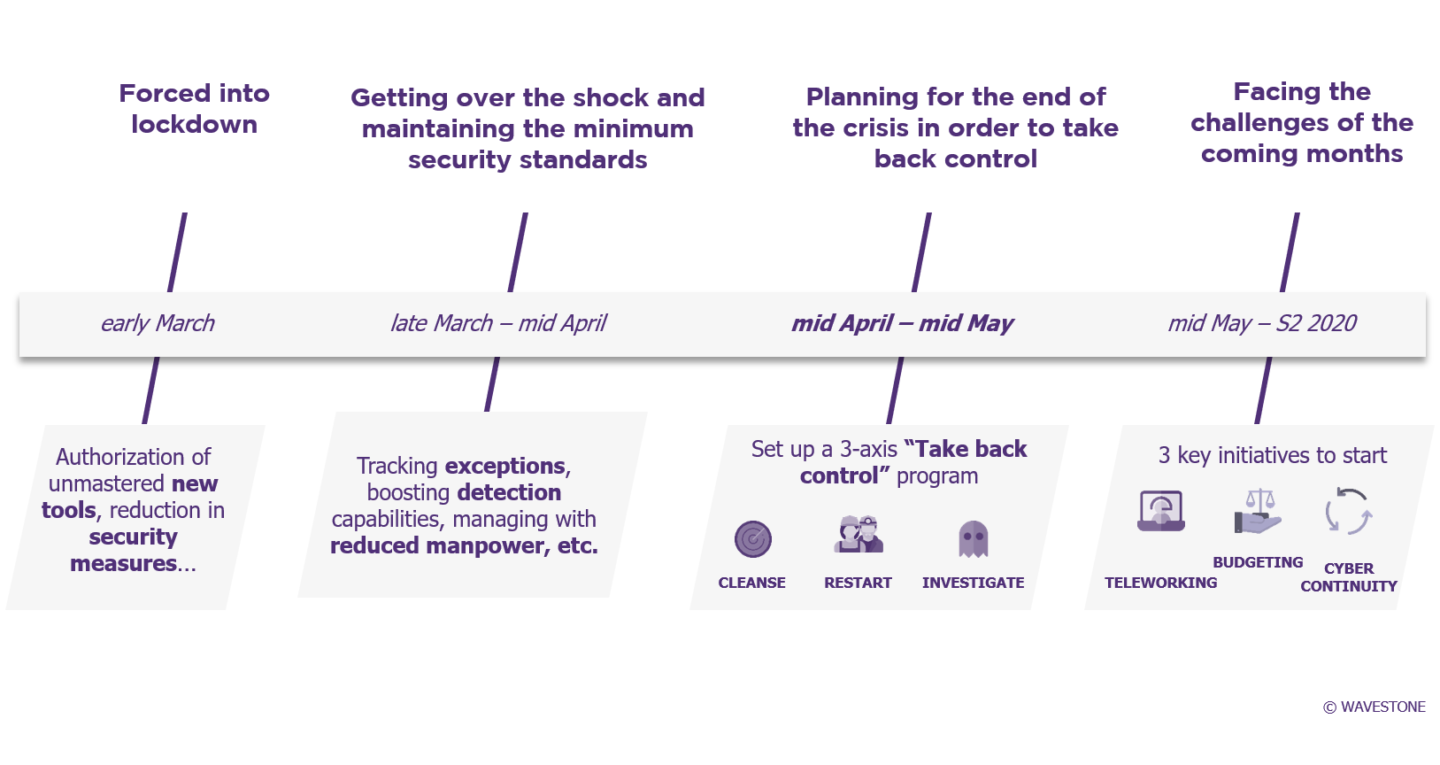
A « Take Back Control » Program
In order for this regaining of control to take place in an efficient, coordinated manner and also in compliance with regulatory requirements, it seems necessary for organisations to structure their actions with the help of a dedicated program based on 3 work streams:
1. Cleanse
Analyze all security exceptions granted and identify any risky situations, design and lead an action plan to remediate or maintain these exceptions and prepare for the regulatory response (GDPR, sectoral regulations, etc.)
2. Restart
Identify and restart suspended security processes: penetration tests, phishing awareness campaign, patch deployment, etc.
3. Investigate
Identify and remedy potential break-ins, by conducting a posteriori investigation, expand the scope of supervision to mass teleworking
A task force and a specific governance
In order to ensure the success of this program, organisations will need to mobilize dedicated resources.
Large international organisations will need to mobilise +/- 4 FTEs for one month (depending on the context). The program should also include daily operational reporting with the CISO to arbitrate, and bi-weekly reporting with the CIO and COO to share the level of risk and reconcile with production/business requirements.
Preparing for tomorrow : teleworking, cybersecurity continuity and budget optimization
Here are three key initiatives to get started:
Extension of teleworking
Current, and possibly future, lockdown measures will accelerate and consolidate this pre-existing trend. To extend teleworking measures, organisations will need to identify weaknesses and evolving needs (third party access, secure authentication, anti DDoS protection, etc.), consider total or partial migration to cloud systems, launch a RFP procedure quickly to take advantage of the sales momentum, and prohibit alternative tools and monitor their use.
The need for cybersecurity continuity
The number of attacks will not decrease, threats will not disappear, a second wave of lockdown measures may occur, and security teams must be able to continue with their activities. It is essential for organisations to define vital activities and resources for all cyber activities, including those stopped during the crisis, make a list of essential suppliers (monitoring, integration, audit, consulting, etc.) and undertake crisis management training with them.
Budget optimization
In the impending economic crisis, many budgets will be cut and it will be essential to demonstrate the efficiency of investments. Proactively reviewing the budget in light of its new priorities is essential. It will also be even more crucial to strengthen the budget/project monitoring and reporting capabilities in order to highlight the benefits of cybersecurity.
All these questions, and many others, will have to be considered in the coming months, but a number of priority projects can be started now. It is often in times of crisis that it is necessary to reinvent oneself, so let’s take advantage of it!