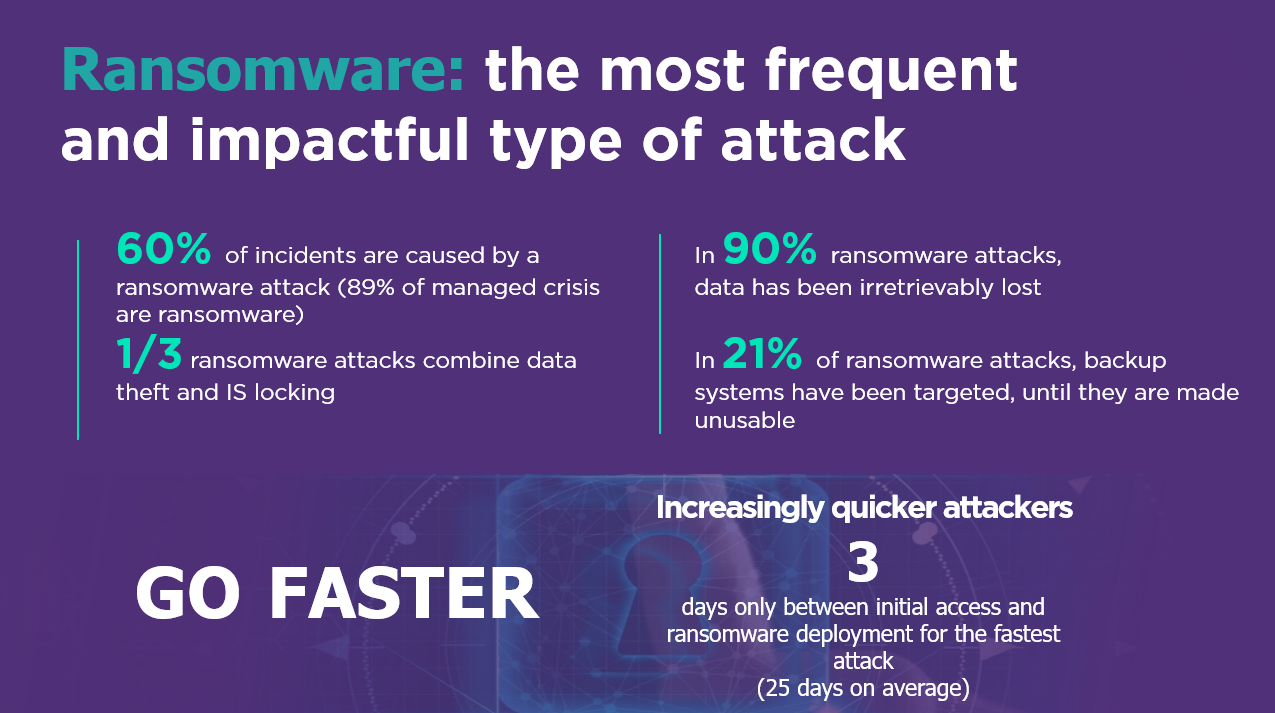
60%
the attacks observed by the CERT-Wavestone are ransomwares
90%
victims have irretrievably lost their data but ransom payments are decreasing
Increasingly quicker attacks: a minimum of 3 days and an average of 25 days between intrusion and blocking
On the launch of the European Cybersecurity Month and for the Assises de la Sécurité (from 13 to 16 October 2021), Wavestone unveils the new edition of its benchmark of cybersecurity incidents. To this end, we reviewed the interventions of the CERT-Wavestone crisis management team between September 2020 and October 2021.
This represents 60 major security incidents that led to business interruption or advanced IS compromise in a diverse sector: industry, public sector, agri-food, information technology, finance, etc. The objective of this benchmark is to shed light on and show the evolution of the state of the cyber threats, whilst also providing the keys for better anticipation and reaction.
A strong preponderance of ransomware in the panorama of cyberattacks
Ransomware accounts for 60% of the cyberattacks encountered by CERT-W for our customers. Furthermore, attackers are becoming increasingly more organized and skilled at carrying out more effective attacks

Gérôme Billois
Partner Cybersécurité
Cybercriminal groups have succeeded in their digital transformation and their organization into a platform has made it possible to majorly make their attacks more efficient and faster
Beyond the simple blocking of the IS, the combination with data theft is becoming more and more present. Indeed, 30%of the ransomware attacks observed include combine the blocking of the IS and the theft of data, the latter being an additional lever to obtain financial gains.
Faster and more targeted ransomware attacks
We see a reduction in the average time between initial access and deployment of ransomware in the system with a minimum of 3 days for the fastest attack and an average of 25 days on managed cases. Attackers are becoming more and more determined to harm their victims. Indeed, they now go so far as to target and destroy the backup mechanisms in order to force the payment of the ransom (21% of cases).
We also find that in 90% of cases data has been irretrievably lost. It should be noted that we are seeing a significant decrease in ransom payments this year (from 20% the previous year to 5% of cases). Multiple factors can explain this decrease, between the better understanding of the low interest to be paid (the payment of the ransom does not accelerate the time of resolution of the crisis), the actions of awareness and pressure on the payment intermediaries by the different authorities.
Other types of attacks are still raging in the background
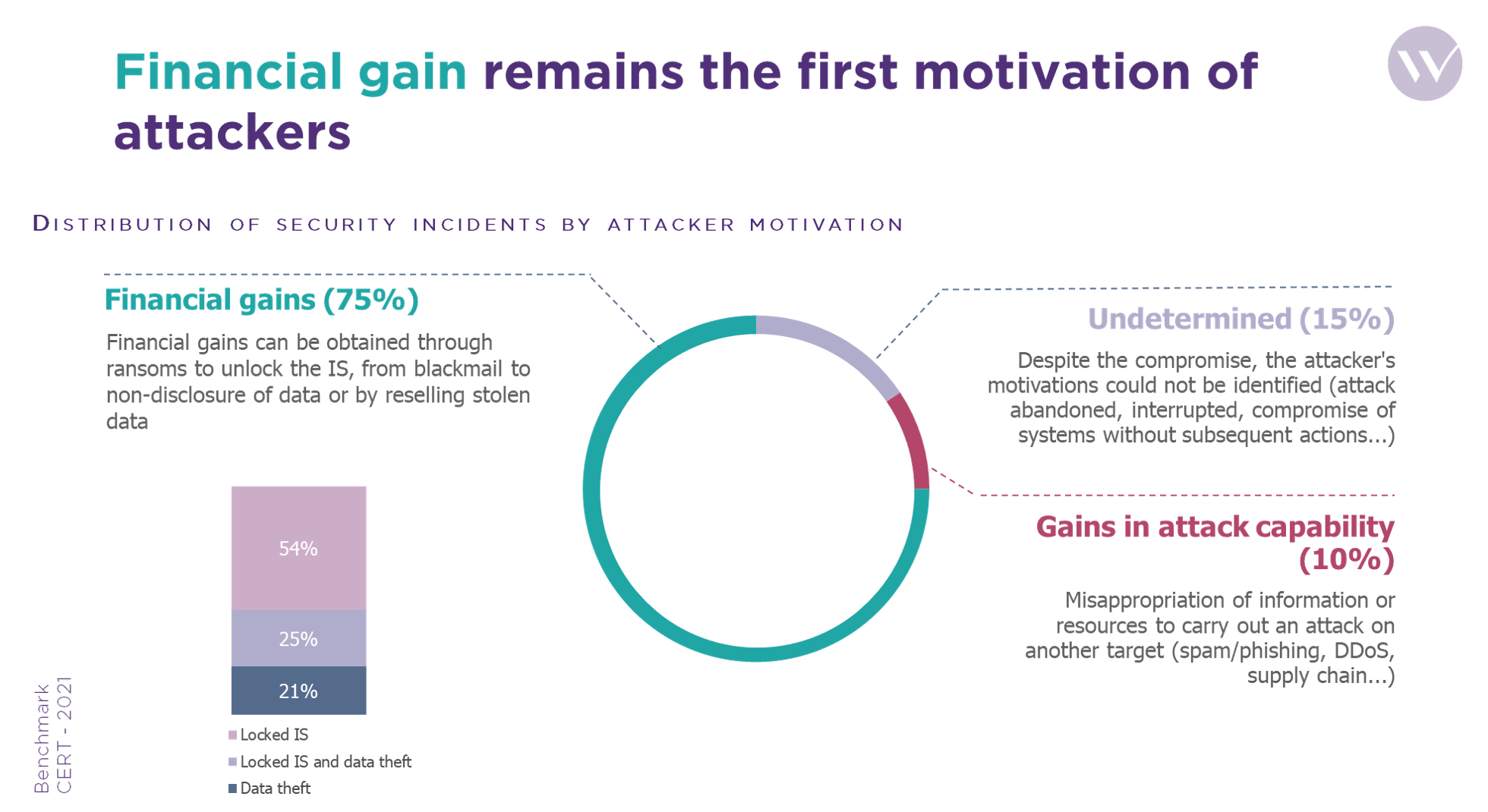
The ransomware threat should not make us forget the attacks of data theft, fraud and the gain in attack capacity that remain well present (25%) even if they are less frequent.
When it comes to accessing channels to break into systems, the main gateways are still the use of valid accounts (23%), fraudulent emails, phishing to obtain information (20%) and remote access services using security vulnerabilities or configuration defects (18%).
How not to be an easy target? Some tips from CERT-W
56% of victims did not anticipate being the potential target of a cyberattack. They did not have an incident response contract or a cyber insurance and 42% of victims had not thought about their resilience in the event of an attack

Nicolas Gauchard
head of CERT-W
Even if diplomatic and judicial actions have weakened the cybercriminal ecosystem, it is not a question of stopping efforts, we must prepare now thanks to simple actions to put in place