We are proud to present our third edition of the Operational Resilience Tooling Panorama. This year has marked a big shift for operational resilience with regulation and market forces at the forefront of driving user adoption.
Our analysis of the tooling landscape reviews market trends and outlines challenges that organisations should be aware of when selecting and implementing an operational resilience tool.
221
Tools across 14 categories, a 15% increase compared to last year
180
Companies included in the radar, a 7% decrease from last year, which could be indicative of mergers and acquisitions
37
New vendors compared to last year
For this edition, we have delved deeper into the tooling landscape to gain a better understanding of the different capabilities offered. To do this, each category has been segmented into 3 different ranges of capabilities covering niche, standard and broad. Our analysis of the current market tooling landscape and experience on the field have enabled us to uncover 4 key trends and challenges.
2023 Operational Resilience Tooling Panorama
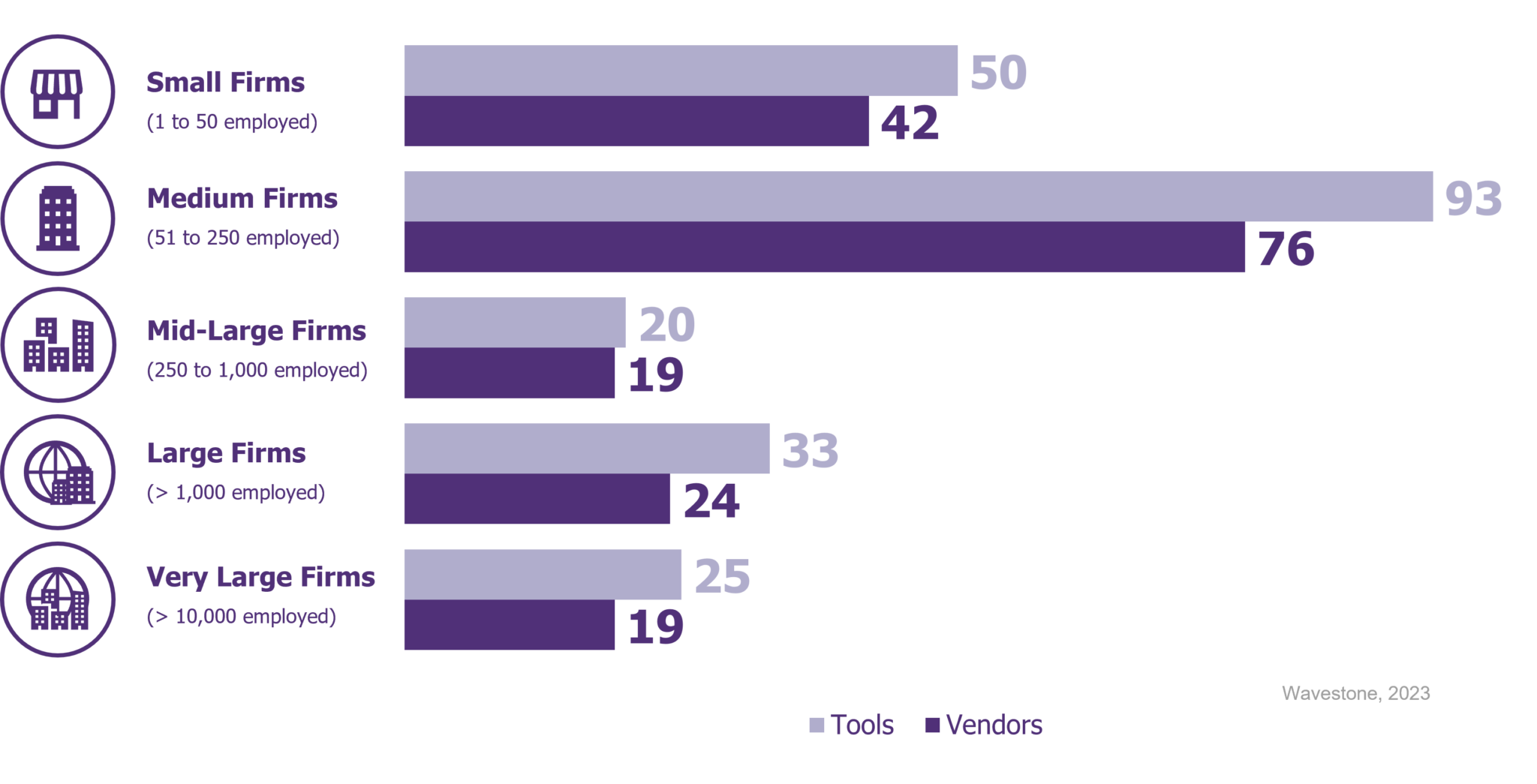
Distribution of tools amongst vendors sizes in 2023
Our vendor selection covers firms from all sizes, with medium firms outweighing others in terms of the proportion of resilience tools offered.
Top 4 Trends
Overall, around 1/3 of market tools cover broad capabilities. Last year there was a rapid consolidation of the market through M&A activity, and in 2023 this trend continued but only for specific categories such as risk management and resilience planning.
Our broad range refers to tools covering more than one resilience capability such as business continuity, incident response, risk management, disaster recovery, crisis management or business process management. It can be worth considering a broad tool for organisations looking to bring everything that is under operational resilience into one platform.
Big players in the market are continuing to expand their offerings to further increase their appeal. Two key examples of this in 2023 include a leading tool provider within Integrated Risk Management (IRM) solutions and another leader within crisis management and critical business communications. Both organisations have each acquired smaller firms that specialise in top-tier business continuity, operational resilience, and risk management capabilities to integrate into their existing platform offering.
This is interesting for organisations who plan to embed BAU operational resilience into existing risk functions as tools within this sphere seem to be designed to help facilitate this transition.
For organisations looking to find one tool to manage their operational resilience, we recommend looking at tools under our risk management, resilience planning and crisis monitoring & response categories. We see this trend remaining as the tooling landscape continues to consolidate itself.
Around 32 tools cover third party risk management with over half of them entering our radar this year. Around 76% of tools in our risk management category cover third-party risk management showing a strong shift to meet regulatory demands.
Regulators are drawing greater attention towards third party risk and its connection to third party resilience. Financial services firms are required to document all third-party dependencies for IBSs, perform risk assessments, and conduct due diligence to inform on concentration risk exposure. UK regulators are also requiring firms to include critical fourth parties in risk assessments.
Most tools in our broad range cover end-to-end third-party lifecycle management. Some tools within this category cover fourth parties and concentration risk. For fourth parties, tooling capabilities include storage of fourth-party information into a central repository, functionality to conduct due diligence assessments and visual mapping of fourth party dependencies. Compliance monitoring and audit management are also included in broad tools where a focus is on risk remediation progress to demonstrate resiliency which will increasingly become a decisive factor for contract negotiations and renewals.
Our standard range includes tools that cover the end-to-end third-party lifecycle management process with risk assessments, vendor due diligence workflows, reporting and analytics. Tools in this range are offering access to data intelligence networks to supplement ongoing monitoring, risk evaluation and assessments. Data intelligence networks enable organisations to obtain a 360-risk view on each vendor through dynamic dashboard reporting.
Other technologies such as automation, data analytics and AI are also commonly found in standard tools. Automation appears to be mostly being applied at the screening and onboarding process. Data analytics seem to be used for vendor selection, risk assessments, performance monitoring and compliance monitoring. AI can be used for intelligent vendor onboarding, due diligence, contract analysis, risk scoring, compliance, and continuous monitoring. A use case could be configuring resilience response workflows using a “if this happens, then do that” programming for when risks arise.
Niche tools for this category covered certain aspects of the lifecycle process including vendor performance management, supply chain risk management, mitigation measures like escrow but also an increased focus on cyber security risk management.
As regulation increases its focus on third-party cloud computing providers, we expect to see some TPRM tools offering features to integrate cloud estate in the near future. Organisations should begin to shift from a compliance-driven mindset to a risk-driven mindset by anticipating this need early.
IBS mapping is a new category addition to our radar with a total of 6 tools covering niche, standard and broad business process mapping capabilities.
Our broad range covers tools that offer scenario testing simulations in addition to standard business process mapping functionalities. The most popular tools on the market are leading enterprise architecture management suite tools that cover multiple capabilities such as governance, risk and compliance (GRC), business process analysis, business capability management, cyber security, and risk management. These tools include collaboration and communication functionalities with customisable workflows and feedback loops. Another capability that falls under this range is reporting and analytics. Broad tools appear to offer a customisable view to focus on operational resilience matters and seem to embed with other resilience capabilities like business continuity and operational risk management.
Our standard range covers process modelling, process analysis, process optimization workflows and integration capabilities with other systems to provide a holistic view of an organisations operational resilience posture. A tool in this category must offer the possibility to map process and technology dependencies and offer drill down functionality for detailed mapping.
Niche tools in our radar cover specific functionalities like compliance mapping, performance monitoring, supply chain analysis as well as application or technology mapping. A niche tool is worth considering for companies looking to embed a specific functionality into their existing tooling landscape.
: We believe there has been a rise in the number of mapping tools as a response to market need, driven by the introduction of regulatory requirements across Europe and Organisations in the UK progressing their operational resilience capabilities.
Around 18% of tools in our radar under our resilience planning and risk management categories cover self-certification functionalities. This shows that there is still room for progress between now and 2025 as financial services firms in the UK approach the FCA’s operational resilience compliance deadline and firms in Europe prepare for DORA.’
Our broad range includes, in addition to those covered in our standard range, functionalities such as KRI libraries for risk management as well as a focus on corrective actions and measures to implement for mitigation and remediation efforts.
Our standard range showcases risk assessments and real time monitoring for risk management tools whilst tools for resilience planning offer self-assessment reporting.
Our niche range of tools cover compliance mapping functionalities and compliance checklists against leading industry standards for cybersecurity (i.e., ISO 27001, NIST…) and operational resilience.
We see this trend continuing to evolve and converge with operational risk with new reporting types being gradually introduced, notably around testing.
Future Outlook
Our analysis and experience within the tooling field suggests 3 key projections on tooling for the near future
1.Niche tools with purposefully designed MI functionality will begin to emerge on the market
As organisations transition from Operational Resilience programmes into BAU, the need to have continuous and automated monitoring of the resilience of their organisation will increase. We suspect that this, along with MI and KRI reporting, will continue to become a key concern for organisations over the next year or two. In response to market need, we anticipate the emergence of new tools that provide a complete and accurate view of resilience gaps; which quantify the potential financial, reputational, regulatory and customer impacts associated with those gaps; and offer a functionality which supports escalation and reporting of those risks to management.
2. Broad tools will increasingly offer resilience testing modules that may not be fit-for-purpose
Following the release of the recent FCA discussion paper “DP3/22 Operational resilience: Critical third parties to the UK financial sector”, which outlines a measure to introduce tools for testing the resilience of material services that CTPs provide to firms and FMIs, we expect to see a rise in the number of broad tools offering testing modules. Some tool providers are already taking this approach, and in our experience, these testing functions are modelled after traditional incident management and escalation tools with a ‘simulation’ option included, which promise to facilitate resilience tests. Broad tools, however, may not be fit-for-purpose, and we believe that niche testing tools, purposefully designed for resilience, will be better suited to address needs in the longer term.
3. Risk management tools will begin to improve third party risk management functionality and fourth party management for reducing the likelihood of systemic risks
If the FCA brings into force the minimum resilience standards for designated CTPs, as outlined in the recent DP3/22 discussion paper, then risk management vendors may tailor their offerings to reflect the new regulation. For instance, if the FCA increases powers of Financial Service firms to request evidence of critical third-party business continuity capabilities, then risk management vendors may update the TPRM modules accordingly. Alternatively, if the FCA implements the ‘framework for the supervisory authorities to identify potential CTPs’, vendors may identify an opportunity to begin tackling systemic risk by increasing functionality to manage fourth parties or identify cloud concentration risks, which is a trend that is already beginning to evolve.