Large organisations are facing unprecedented change, such as adapting to remote working and managing operational risk in a post-pandemic world. Identity & access management (IAM) – the provision and verification of identities and their access rights – is once again at the centre of major transformation programmes. But why exactly is the concept of identity back in the spotlight?
IAM transformation: what are the main drivers?
Businesses are changing at pace, and speed-to-market is strongly dependant on IT systems built on robust and scalable identity services. Whether it’s new a web service available to customers, a significant expansion, or a back-office merger – the requirement to scale IAM services quickly and efficiently is ever-present.
At Wavestone, we witness three drivers, often in combination, which demand more from Identity & Access Management:
- Cybersecurity risks
- Business change
- End user experience
Let’s dive into each of these in more detail.
Information systems are increasingly open and fragmented. Cloud adoption and distributed architectures are contributing to this fundamental shift. Security is adapting its principles and the notion of zero trust is now well established. Identity and access management is a key enabler for zero trust.
Information systems are consumed by thirds parties, customers, and employees. Identity is central to critical data exchange and confidentiality amongst diverse entities. It is therefore necessary to have a unique identity for each entity across the entire information system. While architectures evolve – the ultimate IAM objective does not: the right person or entity, with the appropriate level of rights, to access the right resource, in the right context. Crucially, this principle must be met on an ongoing basis.
Each machine and user’s unique identity is also critical for traceability. An organisation should be able to identify, authenticate and authorise any user, from any other entity, when accessing a resource. The ability to centrally log, audit and monitor these events from across the information system is essential.
Businesses are experiencing core transformation which require more agility & shorter time-to-market. For example, several retailers are seeking new digital avenues to market due to an evolving e-commerce landscape and operational challenges brought about by the COVID-19 pandemic. Identity services must be able to support large business initiatives and cater for innovation at scale.
Complex business change cannot be slowed down by extended security or infrastructure delivery times. Identity must be an enabler, and not synonymous with delay. Any project must be able to rely on identity services which are provided as an available commodity to the business, and not newly designed and deployed for each initiative.
Consolidation and standardisation of IAM solutions and processes is critical to implementing this model. This includes consistent and robust management and is dependent on technology-agnostic methods and protocols – based on the latest, secure, industry standards (such as SAML, OIDC and OAuth).
The provision of identity services must become embedded in the organisation’s operating model and practices such as Agile, DevOps @ scale and innovation @ scale: IAM delivered as a service to the business.
The third, crucial, driver of IAM transformation is user experience. The focus is on organisations to provide employees with the same quality of authentication and authorisation services that external customers have often enjoyed in the past. The objective is to allow end users to prove their identity easily and effortlessly, and access required services, from anywhere, and from any device. This forms the basis for a genuine continuous experience that supports new ways of collaborating, also accelerated by remote working.
Easy and smooth registration processes, as well as consistent authentication across different applications, should be provided to customers to simplify their experience and build brand loyalty. This same principle holds for employees and third parties.
Passwordless technologies and unique application logins are examples of solutions on the rise; Innovative risk-based and contextual approaches can streamline accesses, which can have a significant, positive, impact on user experience by reducing authentication requests.
What steps to IAM transformation?
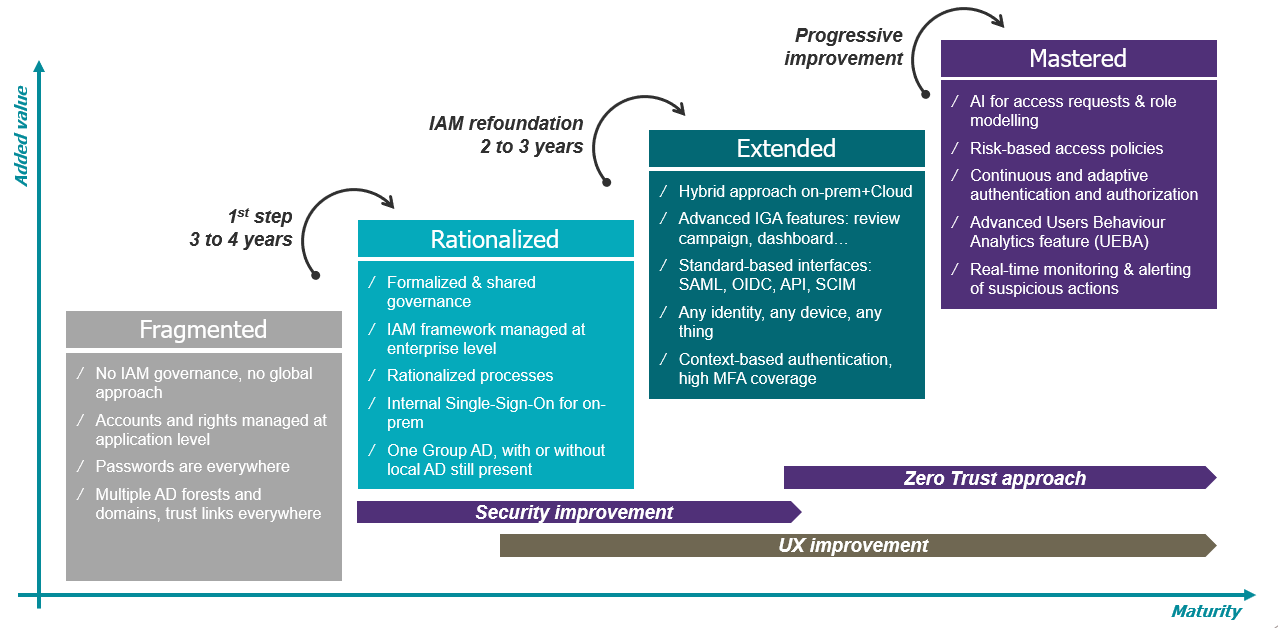
Understanding your current maturity is a key step towards delivering on the above. Over years of supporting IAM initiatives with clients, we have built our IAM maturity improvement journey, which is comprised of 4 maturity steps.
- Fragmented: the organisation lacks a consolidated approach to IAM across solutions, governance, and standards.
- Rationalized: the technology landscape supporting IAM is simplified and managed centrally to aid user experience across all applications and users. Consolidation provides satisfactory oversight capabilities.
- Extended: the organisational IAM capabilities cater for an evolving information system: any user, any device, any service.
- Mastered: the organisation has adopted next-gen solutions, which provide strong security benefits and a smooth user experience – all whist reducing the workload on IT operations thanks to intelligent automation.
Final thoughts
Each of the above steps requires a deep transformation of the environment: change of governance, change of processes, and deployment or migration of supporting technologies. To be a success, we believe it needs to be addressed as a dedicated IAM transformation programme.