Since our last CISO radar, the world and economy remain in an extremely complex health crisis: the persistent enforcement of health protection measures, a rise in geopolitical tension, acceleration of digital transformation, strong economic recovery…. These elements all have an impact on cybersecurity and the respective actions that large organisations must take to ensure robust cybersecurity. However, like any crisis, the health crisis also provides the opportunity to plan and prepare for the future.
From a cybersecurity perspective, due to the range of cyber-attacks observed and the vulnerabilities they rely on, short-term priorities remain to focus on basics, namely having knowledge in one’s Information System, basic hygiene rules, vulnerability management, patch management, backup testing or crisis exercise. However, once those basics implemented, we wanted to summarise the trends observed in the market and among our clients to help you identify the areas of focus from 2022 onwards.
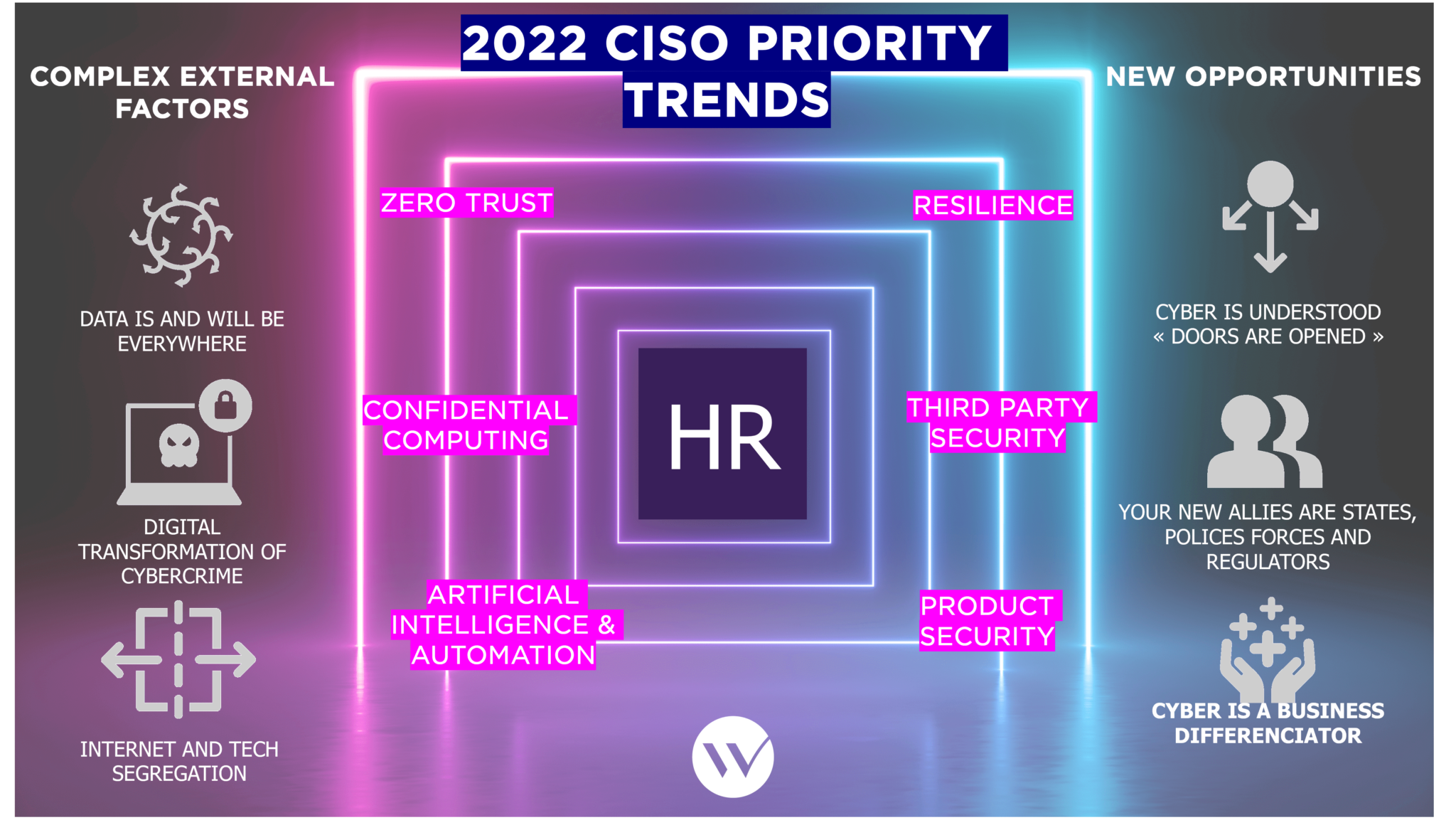
Complex External Factors: Threat Transformation, Data Dispersal and the Increase of Digital Sovereignty
Threat Transformation
As expected, cybercrime continues to grow and is becoming more complex, impacting the entire economic landscape – from small-medium sized businesses to large companies and local authorities. In 2021, CERT-W has observed an increase in cyberattacks and, in particular, attacks via ransomware and pay-as-you-go espionage platforms.
With regards to the increase in the number of attacks, we observed in 2021 that these attacks not only blocked the victims’ IS which may have resulted in data leaks, but also sometimes directly or indirectly impacted the victims’ backup systems. This trend is derived from our benchmark where we observed that 21% of the incidents handled by CERT-W last year involved direct or indirect impact to the backup systems, which complicates all the more crisis management processes. Additionally, critical vulnerabilities have also multiplied in 2021 – where these vulnerabilities are exploited and installed in a mere few hours (e.g. the latest Log4j vulnerability).
As for attacks conducted via “pay-as-you-go” espionage platforms, a great example to name would be the Pegasus Project Revelations in India, whereby several state actors used a spyware developed by an Israeli technology firm to spy on the mobile phones of thousands of political and public figures. The ease of execution and relative cost of this type of attack makes it possible for companies to be attacked as well.
What these trends signify is that cyber-attackers are undeniably becoming a real profession, and that there is a shift in the scale and magnitude of cybercrime driven by profitability, which ultimately motivates further developments in the cybercrime ecosystem. Thus, the environment in which we operate in today is undeniably riskier: the means and mechanisms in which a cyber-attack can be initiated are more advanced, complex and accessible by a large spectrum of threat actors.
Data dispersal
The acceleration of digital transformation has formulated the concept of “Extended Enterprise”, whereby data is multiplying and becoming more dispersed among different third parties with varying degrees of control. For instance, organisations are increasingly embracing and adopting the use of Cloud technologies for different purposes (e.g. IaaS, PaaS, SaaS). However, depending on the Cloud model adopted (e.g. Public, Private or Hybrid Cloud), the degree of control over the security mechanisms that are implemented to protect the organisation’s data will vary.
As a result, architectures are also becoming more diverse and complex, and organisations are finding it more difficult to obtain an exhaustive view of all their entity’s data, how it is being protected and how to keep control of it (e.g. on identity and access management issues).
Digital Sovereignty
2021 has seen a strong desire to establish digital sovereignty in many countries. Ultimately, the motivations for establishing digital sovereignty are different between countries, but the effects are similar – with the multiplication and reinforcement of digital borders and the obligation to localise data, this calls into question the ambition of large companies to build a fully integrated IS. In response to this, governments and major international digital providers are launching more projects aimed at creating regional or national platforms that are more or less sovereign. For instance, in 2021 – ServiceNow announced a multi-million euro investment to enable its customers to have more control over their EU hosted data – that is, customers have the option to choose whether they want their data to be handled only within the EU. This investment was partly driven by a shift in political landscape and regulatory dynamics (e.g. Schrems II on EU-US Privacy Shield, Brexit) which calls for greater data localisation capabilities and therefore leads to a shift towards data and digital sovereignty.
Increasing Opportunities: The Launch and Mobilisation of Cybersecurity Initiatives by Governments and Organisations as Cybersecurity is increasingly being perceived as a Business Differentiator
Perhaps one of the most significant developments in 2021 is that we see governments placing greater emphasis on cybersecurity. In fact, governments across the world are mobilising significant budgets with the aim of enhancing cybersecurity – for instance, UK’s 2021 Autumn Budget and Spending Review (which covers UK’s government spending from 2022-23 to 2024-25) published by HM Treasury has recorded a £114 million spending increase in the National Cybersecurity Programme, and in total the UK Government is investing £2.6 billion in its cyber and legacy IT.
In addition, with growing number of organisations in the economy, cybersecurity is now perceived as a business differentiator. Cybersecurity is seen as a key element in the sales process in many industries (e.g. cybersecurity embedded within contractual clauses, requirements in specifications, etc.). Some companies are even launching cyber offers to support the development of new companies. This phenomenon is leading to additional budgets being allocated just for cybersecurity related initiatives and changing the way in how the subject is perceived and dealt with in large organisations.
In this context, what actions should be prioritised?
As aforementioned, many organisations still need to prioritise the implementation of basic security and hygiene rules to avoid being an easy target that is susceptible to attacks. However, beyond this, we have also identified several key topics, both at the organisation and technical level, that organisations will have to consider within their cybersecurity streams in their medium-term strategy.
Firstly, cyber-resilience is and will remain a top priority for organisations both at the business and technical level. Cyber-attacks are becoming more prominent, and their impacts are becoming increasingly damaging and devastating. With more organisations adopting isolation policies when impacted by an attack, they risk being isolated by its ecosystem. Hence, it is imperative for organisations to:
- Identify the most critical assets and business processes
- Review continuity plans in the face of new attacks
- Accelerate the recovery phases
These challenges need to be addressed and discussed with the business to identify continuity solutions that can be applied in the event of a long IT failure (e.g. between 2 – 3 weeks). The idea is to establish a continuity solution that is realistic and achievable while also prioritising and considering the impacts to the business, organisation and customers.
From the IT department’s point of view, the priority with regards to resilience should be implementing a containment strategy, accelerating the recovery of critical assets (cf. the white paper co-authored by Wavestone and Microsoft on DBA security) and preparing robust and efficient backup systems.
In addition, securing interactions with third parties, in the broadest sense, must also be a priority. Organisations interact with many suppliers, some of which are critical from a technological point of view (software publishers, outsourcers, etc.). As a result, suppliers are becoming targets of cyber-attacks as attackers can exploit and capitalise on the supplier’s systems to penetrate the organisation’s IS to reach their final objective. Therefore, companies must develop the capacity to easily, yet comprehensively, evaluate the security level of their suppliers, both in terms of the services and systems provided by the supplier, while also preparing to manage incidents. With regards to evaluating the security level of suppliers, many different solutions are emerging but are not fully developed as of today. As a result, companies must update and enhance their own internal security and risk evaluation processes to continuously integrate new and emerging risks, in particular, the risk of relay attacks on third-party technology suppliers (e.g. SolarWinds and Kazeya attacks). Today, there are no simple solutions identified and the verification of the integrity and safety of software codes supplied by third parties is manual and time-consuming. Thorough due diligence combined with continuous evaluation and prompt reaction must be applied to all areas deemed particularly sensitive to manage risks.
What are the main technological directions that will lead to greater security in the medium term?
The security principles bolstered by Zero-Trust is a solution to the challenges caused by “Extended Enterprise” and data dispersal. These challenges necessitate in-depth changes in the security model, which also implies necessary changes and work around infrastructure, workstations, applications and identity and access management (IAM) model. The notion of Zero-Trust is based on services that enable central verification of the identity of persons or services accessing the data and the level of compliance required which in turn is dependent on the location or device used. Initial projects around implementing Zero-Trust strategy show some successes in different sectors: implementation of conditional access to Cloud resources or for remote access, first micro-segmentation studies, etc. 2022 will be the year for organisations to comprehensively define and formalise their Zero-Trust strategy, and to define the strategy’s progress by integrating it into major IS developments.
In addition, AI and automation will be essential to reinforce the general security level in an environment where we see threats rapidly and permanently evolving today. With the usage of AI and automation, it will also enable different teams to focus more on high added-value work. Today, there is still a wide gap between the speed in which a cyber-attack takes place versus that of when the attack is detected. Moreover, in the context of skills shortage, teams must be able to free themselves from manual and time-consuming tasks. Thus, not only would automation be essential in the processes of detection, reaction and recovery following an attack, but also in the mechanisms for assessing levels of cybersecurity. AI and automation are also formidable tools for cost optimisation and rationalisation and are therefore the preferred choice by management within the organisation. However, in adopting AI and automation, organisations should also pay particular attention to their impact on the responsibilities between different teams and ensure the security and quality of the automation.
Lastly, confidential computing will eventually amalgamate different technologies available to increase the level of trust in data processing systems in the medium term, especially within the Cloud. There is currently massive research being conducted on the subject (new encryption algorithms, key management systems, security within processes, memory, attestation of conformity of hardware or software, etc.) which could potentially be solutions to reduce the legal risks associated with using digital services. These technologies would go well beyond concepts such as “Bring your own Key” that are put forward by certain publishers, but which provides little protection against the legal risks associated to the access of data by the authorities.
2022 Priority: Human Resources
The key issue in 2022 will undeniably be related to a shortage on human resources. The shortage of cyber skills on an international scale poses a real problem for large organisations and their suppliers. The industry is facing a challenge in sourcing and diversifying profiles on all criteria, including academic training. Cyber is no longer just a technical field, but touches on a plethora of subjects: operational resilience, fraud, risks, governance, etc., and goes beyond the context of an organisation (e.g. cyber for good, digital sobriety, etc.). As a result, many diverse and interesting career paths are emerging.
Countries are offering solutions at a national level through creating training courses and awareness-raising efforts in an effort to make cybersecurity a more attractive subject and therefore bolster the growth of the field. However, a lot more efforts and actions need to be taken at the organisational level. It should also be noted that it is often necessary to adopt a two-dimensional approach for two different types of audiences: the cyber specialists who are already good technically and looking for more advanced challenges, and the generalists where more educational -and training efforts need to be prioritised in the short and medium-term. The HR strategy will have to be adapted according to these two audiences, taking into consideration different factors such as attractiveness, retention, career paths, training, recognition, etc.
With regards to attractiveness, organisations must adopt a tailored approach to recruitment. Job descriptions and remuneration need to be reviewed, and more importantly cybersecurity as a field and subject needs to be promoted internally within companies.
In terms of retention, the industry must be able to promote and establish cybersecurity as an engaging and exciting career path. Tasks need to be reviewed, diversified and distributed between different areas and teams to ensure efficiency and retain interest.
In 2022 and the upcoming years, cybersecurity will continue to be at the centre of the discussion. With our world leaders now recognising and paying more attention to cybersecurity, combined with the actions we have taken to ensure we are better prepared to face and are more resilient against cyber-attacks – we are progressing towards the right direction. It is up to us to continue to anticipate, adapt and develop new strategies to tackle new evolving threats, and in doing so we can better position ourselves to face any challenges that we may encounter in the future.
Methodology
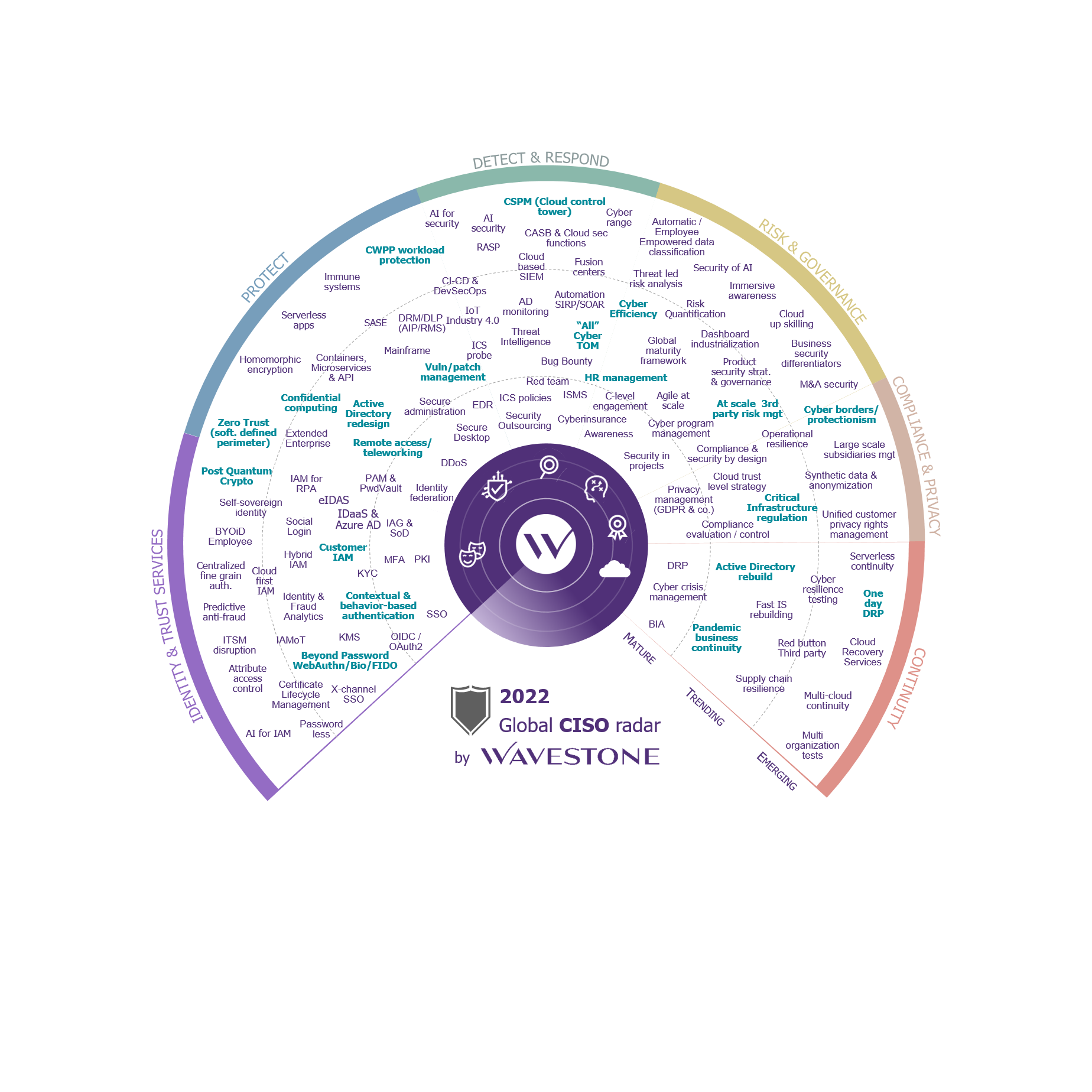
The CISO Radar is a tool that Wavestone has developed and published since 2011. More than 40 experts meet three times a year to discuss news and key topics, based on what they’ve observed while working with Wavestone’s clients. This assessment includes all Wavestone’s offices – from New York to Hong Kong – taking in Paris and several others.
Every year, the Radar presents a broad selection of the topics that CISOs must grapple with in their role. It covers over 100 subjects, which are considered and analysed by our experts.
It’s presented as a series of dials covering key themes (identity, protection, detection, risk management, compliance, and continuity) on three levels: Mature, News, and Emergent. The “Mature” level covers topics that every CISO can, and must, master. The “News” level covers topics currently being addressed; these are new areas where initial feedback can be shared. The “Emergent” level covers topics on the horizon that are still little known or that have no obvious solutions. These topics are included to better predict future developments and prepare for their emergence in organizations.