Swiss cyber startups are ready for Quantum & Post-Quantum Cryptography
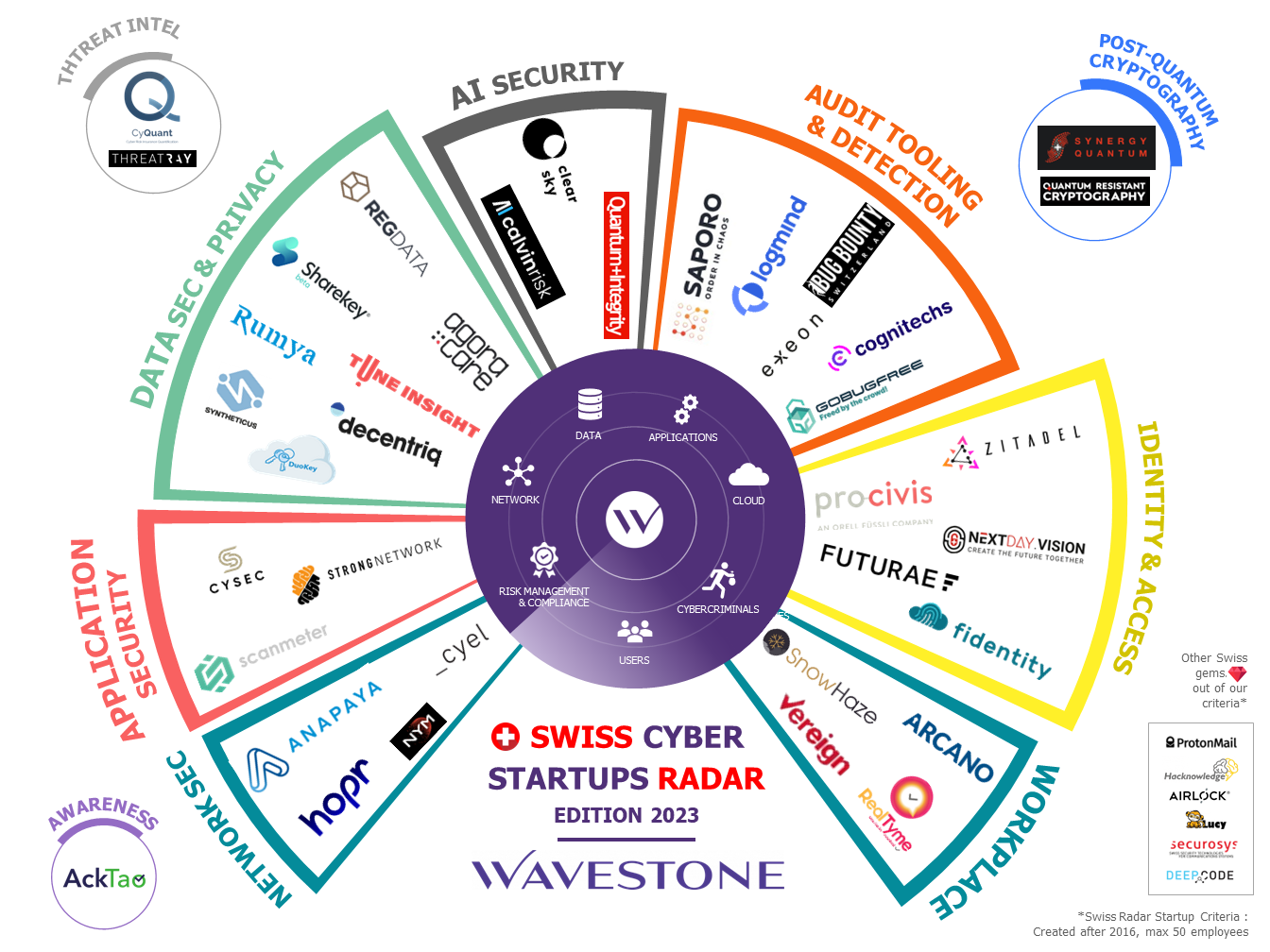
Every year since 2020, Wavestone identifies Swiss cybersecurity startups in its eponymous radar. The 2023 edition sees the rise of post-quantum cryptography, a technology that will become fundamental for security strategies in the near future.
With acceleration in quantum computing, current cryptographic algorithms will no longer provide sufficient security guarantees. A sufficiently advanced quantum computer would be able to break state-of-the-art key exchange in a matter of hours. While such computers will not be available for years, it is crucial to be ready.
Efforts are currently being made to invent and deploy post-quantum cryptography (PQC), based on mathematical problems that are as difficult to solve for quantum computers as for classical ones. While PQC is implemented on classical computers, a separate class of algorithms is also developed and run on dedicated hardware: quantum cryptography. It uses the principles of quantum mechanics – namely quantum superpositions and entanglement – to ensure security even if an attacker had an infinitely powerful computer, be it classical or quantum.
Switzerland, as a hub for innovation and technology, is well positioned to take advantage of these developments. Two Swiss startups, QRCrypto S.A. and Synergy Quantum S.A., are working in these fields. QRCrypto S.A. is developing PQC solutions that cover both symmetric and asymmetric cryptography, as well as offering 5G compatible, post-quantum secure SIM cards. Meanwhile, Synergy Quantum S.A. is working on both quantum encryption and PQC and is part of the Microsoft for Start-ups Program.
These high-impact industry solutions will revolutionize secure communications and ensure the protection of sensitive data in the years to come.
Key figures
38
Swiss startups
78mCHF
total fundraising (public data)
2019
average date of fundation
13
employees on average
Startups joining the cyber radar in 2023
Swiss innovations are a mirror of the post-pandemic world
- A company’s building is not its only workspace anymore, as people may come to the office or stay at home. This directly impacts authentication and access management and thus cybersecurity strategies.
- Collaboration has migrated from the “real world” to the digital one, thanks to online platforms such as Microsoft Teams or Zoom. The latter needs to provide secure and encrypted communications to guarantee confidentiality of professional discussions.
- As people use personal and professional devices, data is transferred to multiple devices. Hence, data transfer solutions must evolve to provide higher security and compatibility.
Geographical focus: undisputed predominance of Lausanne and Zurich
Unsurprisingly, most startups are located around two main technological clusters: Zürich and Lausanne. This confirms an already existing trend since these two cities are hosting Swiss Federal institutes of technology (ETHZ in Zürich, EPFL in Lausanne).
These universities are providing a fertile ground for startups as they offer support in terms of infrastructure but also in terms of collaboration with students and labs. In return, intellectual property is shared between startups and universities. This model is a success for Switzerland as it allows to continuously improve the economy of these regions with a good balance between investment and research.
Methodology
Wavestone’s Swiss Cybersecurity Startups Radar identifies new players in the Swiss cyber innovation ecosystem. Its objective: to provide a global and critical view of an ever-renewing environment.
- Head office in Switzerland
- Less than 50 employees
- Less than 7 years of activity (established as of 2016)
- Business model around a specific product (software or hardware)
- Open Source Intelligence (OSINT) data consolidation
- Evaluation in regard to above criteria
- Qualitative interviews with the startups
Key takeaways
- Swiss startups are adapting their solutions to an increasingly remote world, with a strong predominance of data and network security topics.
- To meet the challenges of software security, Swiss startups are increasingly relying on the Open Source model.
- Swiss startups are building the future of Identity and Access Management (IAM) thanks to Self-Sovereign Identity (SSI).
- Lausanne and Zurich remain at the heart of the Swiss startups landscape.
These evolutions have had a direct impact on the cybersecurity startups landscape. Indeed, most startups are now focusing on a few topics:
40%
startups develop IAM and Workplace solutions
30%
of startups innovate in Data and Network Security
Open Source, a growing response to new cybersecurity challenges
A naïve perception of IT security is called “security by obscurity”. It relies on the belief that if a system remains private and unknown, it would be harder for an attacker to compromise it. This idea is, of course, a myth since vulnerabilities can be discovered without any prior knowledge of a system. Open Source is the exact opposite: source code is public and maintained by a community or a company, which can sell services associated with this solution.
Is Open Source Software reliable?
- Open Source is an improvement in terms of auditability as code is regularly reviewed. However, regular code review cannot replace an exhaustive security audit.
- OSS are quickly patched thanks to the consistent work provided by the community. However, this improvement in terms of security can bring complexity of deployment, especially if the software is not binded to a professional support service.
- Open Source's killer feature? It's easy to check whether an open-source program has implemented a backdoor or not, since one just has to look at the code and see for oneself. Unfortunately, it is not always that simple: there is no guarantee that the published source code is the code that is run by Software-As-A-Service (SaaS) platforms.
Limits of the open source model for cybersecurity
Some Swiss startups, such as Zitadel, have evaluated that the Open Source model was overall the best option for their product. Companies should keep in mind that security audits, qualified support services and inventory of associated 3rd party libraries are still required when implementing an Open Source security software!
Improving IAM with Self-Sovereign Identity
Among the startups added in our radar in 2022, we also noticed a surge in Self-Sovereign Identity solutions – such as ProCivis. Self-Sovereign Identity (SSI) is a relatively new concept and may represent the future of Identity and Access Management (IAM).
To understand it, let’s go back through the history of IAM.
From centralized IAM to blockchain-based identity management
The most basic authentication mechanism is a traditional centralized model. When users would like to access any service provided by an external company, they first need to register by sending personal data. Then, they can authenticate and benefit from the required feature. One of the main drawbacks of this model is that users need to send personal data to possibly dozens of companies, without having any control on it.
The identity provider (IdP) model offers improvement. Here, users register to only one third-party company. Then, when they would like to access a service, authentication is performed by this third-party – only necessary data is sent to the final service provider. This is still not perfect, as users do not keep direct control of their identification data.
In the Self-Sovereign Identity (SSI) model, data is decentralized in the blockchain: users register their data with an ID certifier guaranteeing data’s authenticity. Then, when users authenticate to a service, the provider can use this data stored in the blockchain. In this case, users have full control on their data and decide which information can be retrieved by service providers.
SSI: the new digital passport
- Regarding data privacy, they do not need to store and manage user data anymore, as everything is hosted in the blockchain. This simplifies confidential data management and helps to comply with data privacy laws such as GDPR (General Data Protection Regulation) in Europe or FADP (Federal Act on Data Protection) in Switzerland.
- Regarding infrastructure, they do not need to deploy and maintain technical components dedicated to the authentication. Since everything is managed by SSI’s decentralized architecture, service providers only need to setup connectivity with the blockchain.
- Regarding interoperability, SSI tends to be the unique authentication system gathering all service providers at the same place. This significantly reduces the work for companies and organizations which rely on multiple identity providers. Indeed, compatibility with third-party providers such as Microsoft Azure or Okta is irrelevant as long as an access to the blockchain has been configured.